- These list items are microformat entries and are hidden from view.
- https://dltj.org/article/ssh-as-socks-proxy/
- Dear future self,If you are reading this, you are remembering a time when you ran into a really nasty interception proxy ((Version of the "Proxy Server" Wikipedia page when this posting was written)) and you are looking for a way around it. Do you remember when you were sitting in the Denver International Airport using their free wireless service? And remember how it inserted advertising banners in HTML frames at the top of random web pages as you surfed?After about a half an hour of this, you started looking for solutions and found that the secure shell client can act as a SOCKS proxy ((Version of the SOCKS Wikipedia page when this posting was written)). Using 'ssh', you set up a tunnel between your laptop and a server in the office that encrypted and effectively hid all of your network communications from the interception proxy. And if you are reading this again you want to remember how you did it.Set up the SOCKS proxySOCKS is a client protocol that can be used to tunnel all of your traffic to a remote host before it fans out across the internet. The OpenSSH client can set up a local SOCKS proxy that uses an 'ssh' session as the network tunnel. To set up the tunnel, use the -D option followed by a local port number: ssh -D 9050 [username]@[remote.server.name]To refresh your memory, here is an extract from the 'ssh' manual page for the -D option:-D [bind_address:]portSpecifies a local "dynamic'' application-level port forwarding. This works by allocating a socket to listen to port on the local side, optionally bound to the specified bind_address. Whenever a connection is made to this port, the connection is forwarded over the secure channel, and the application protocol is then used to determine where to connect to from the remote machine. Currently the SOCKS4 and SOCKS5 protocols are supported, and ssh will act as a SOCKS server. Only root can forward privileged ports. Dynamic port forwardings can also be specified in the configuration file.Using the SOCKS proxyNext you need to tell the applications to use the SOCKS proxy. If you are still using a Mac when you are reading this, you'll probably have it pretty easy. Mac OSX lets you set a proxy system-wide that all well-written Mac applications will use to get their parameters. It is in the "Proxies" tab of the Advanced... network settings. On Mac OSX version 10.5 (Leopard), it looks like the graphic to the right.If you're using some sort of UNIX variant, the application may have a setting to use a SOCKS client, or you may need to use the 'tsocks' shim that intercepts the network calls of the application. And, future self, if you are using a Microsoft Windows box right now, please remember how much simpler life was when you used a Mac or Linux desktop. If you find yourself in such a spot, some reader of this blog posting may have left a comment for you below that will help you use a SOCKS proxy with a Windows platform.Hope this helps. Sincerely,Self, circa February 2008
- 2008-02-18T22:12:56+00:00
- 2018-01-15T22:35:29+00:00
Note to Future Self: Use ssh -D to bypass annoying interception proxies
Dear future self,
If you are reading this, you are remembering a time when you ran into a really nasty interception proxy ((Version of the "Proxy Server" Wikipedia page when this posting was written)) and you are looking for a way around it. Do you remember when you were sitting in the Denver International Airport using their free wireless service? And remember how it inserted advertising banners in HTML frames at the top of random web pages as you surfed?
After about a half an hour of this, you started looking for solutions and found that the secure shell client can act as a SOCKS proxy ((Version of the SOCKS Wikipedia page when this posting was written)). Using 'ssh', you set up a tunnel between your laptop and a server in the office that encrypted and effectively hid all of your network communications from the interception proxy. And if you are reading this again you want to remember how you did it.
Set up the SOCKS proxy
SOCKS is a client protocol that can be used to tunnel all of your traffic to a remote host before it fans out across the internet. The OpenSSH client can set up a local SOCKS proxy that uses an 'ssh' session as the network tunnel. To set up the tunnel, use the -D option followed by a local port number:
ssh -D 9050 [username]@[remote.server.name]To refresh your memory, here is an extract from the 'ssh' manual page for the -D option:
- -D [
bind_address:]port- Specifies a local "dynamic'' application-level port forwarding. This works by allocating a socket to listen to
porton the local side, optionally bound to the specifiedbind_address. Whenever a connection is made to this port, the connection is forwarded over the secure channel, and the application protocol is then used to determine where to connect to from the remote machine. Currently the SOCKS4 and SOCKS5 protocols are supported, and ssh will act as a SOCKS server. Only root can forward privileged ports. Dynamic port forwardings can also be specified in the configuration file.
Using the SOCKS proxy
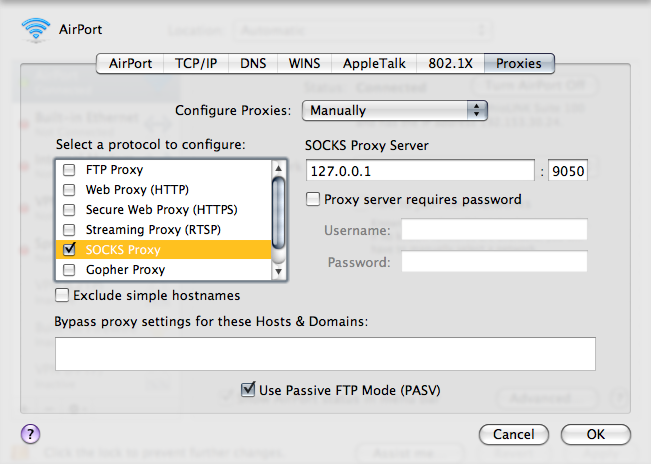
Next you need to tell the applications to use the SOCKS proxy. If you are still using a Mac when you are reading this, you'll probably have it pretty easy. Mac OSX lets you set a proxy system-wide that all well-written Mac applications will use to get their parameters. It is in the "Proxies" tab of the Advanced... network settings. On Mac OSX version 10.5 (Leopard), it looks like the graphic to the right.
If you're using some sort of UNIX variant, the application may have a setting to use a SOCKS client, or you may need to use the 'tsocks' shim that intercepts the network calls of the application. And, future self, if you are using a Microsoft Windows box right now, please remember how much simpler life was when you used a Mac or Linux desktop. If you find yourself in such a spot, some reader of this blog posting may have left a comment for you below that will help you use a SOCKS proxy with a Windows platform.
Hope this helps. Sincerely,
Self, circa February 2008