PPTP VPN for iOS with AT&T Uverse and DD-WRT
Wandering into public or semi-public wireless networks makes me nervous because I know how my network traffic can be easily watched, and because I'm a geek with control issues I'm even more nervous when using devices that I can't get to the insides of (like phones and tablets). One way to tamp down my concerns is to use a Virtual Private Network (VPN) to tunnel the device's network connection through the public wireless network to a trusted end-point, but most of those options require a subscription to a VPN service or a VPN installed in a corporate network. I thought about using one of the open source VPN implementations with an Amazon EC2 instance, but it isn't possible with the EC2 network configuration judging from the comments on the Amazon Web Services support forums. (Besides, installing one of the open source VPN software implementations looks far from turnkey.) Just before I lost hope, though, I saw a reference to using the open source DD-WRT consumer router firmware to do this. After plugging away at it for an hour or so, I made it work with my home router, a AT&T U-verse internet connection, and iOS devices. It wasn't easy, so I'm documenting the steps here in case I need to set this up again.
Prerequisites
To make this happen, I'm using a D-Link DIR-825 that has been flashed with "v24-sp2 (04/23/10) std" of the DD-WRT firmware. For my internet connection I have a AT&T U-verse residential gateway and a "Max Turbo" plan (I work from home so I need the 3 Mbps uplink speed that is only available with "Max Turbo", although that added uplink capacity is certainly helpful for this road-warrior VPN use). I also have a pair of iOS version 4.3.3 devices; this setup might work for other handheld operating systems (e.g. Android or Windows Mobile), but I don't have any of those to test with.
DD-WRT comes with support for a point-to-point-tunneling-protocol (PPTP) server. I know PPTP has some inherent security risks. At this point I'm just aiming to be harder for someone passively listening on the public wireless network to eavesdrop on my connections. I'm not doing anything ultra-sensitive that I need advanced encryption; I just don't want to make it easy to watch what my devices are doing.
Setting up the AT&T U-verse Residential Gateway
Since the D-Link router is behind the U-verse residential gateway, we need to punch a couple holes through its firewall to allow downstream connections from the iOS devices to reach the D-Link router. Specifically, one needs to forward ports 1723/TCP and 1723/UDP through the residential gateway firewall to the internal D-Link router. To do this:
- Connect to the web interface of the residential gateway, select the Settings tab followed by the Firewall tab then the Applications, Pinholes and DMZ tab.
- This screen has two steps: 1) Select a computer; then 2) Edit firewall settings for this computer. Click on the link to "Choose" the DIR-825 router (by name).
- In the second step choose the "Add a new user-defined application" link. Use "PPTP" for the Application Profile Name.
- Select "TCP" and put "1723" in the From text box, under Application Type select PPTP virtual private network server and leave the rest of the boxes blank for the defaults; click on Add to List.
- Repeat everything in the last step except choose UDP in place of TCP.
- Click on the Back button to return to the Allow device application traffic to pass through firewall screen.
- Select the Allow individual application(s) radio button, click on the User-defined applications list, pick "PPTP" from the Application List, and click on Add.
- Click Save.
The U-verse residential gateway will now pass everything inbound on ports 1723/TCP and 1723/UDP to the D-Link router. You're done with the residential gateway setup now.
Setting up the PPTP Service on DD-WRT
Now we need to set up the DD-WRT PPTP service. This is harder than it probably should be, but given the geeky focus of the DD-WRT effort (in my humble opinion), features seem to come before user interface and documentation niceties. This works for me, but it isn't entirely clear or easy, and I can't offer troubleshooting insights if it doesn't work for you. It has two main steps -- first, turn on and configure the PPTP server; and second, patch the PPTP server configuration with a start-up script so that it actually works. First, the PPTP server configuration:
- Log onto the DD-WRT web interface, select the Services tab then the VPN tab.
- Enable PPTP Server, Broadcast support, and Force MPPE Encryption.
- Put in the WAN IP (listed in the upper right corner of the web page) in the Server IP box. (Some instructions I have seen said that this can be left blank and the firmware will automatically pick it up. That didn't work for me.)
- For Client IPs, put in a range of LAN-side IPs that aren't being used by the DHCP server. In my case I'm using "192.168.68.200-210".
- Put in one or more CHAP-Secrets. These are the username and passwords used on the PPTP client to connect to this server, and they follow a weird form: username-space-asterisk-space-password-space-asterisk. For example:
1username * password * - Leave Radius disabled.
- At the bottom of the screen, pick Apply Settings.
The second step is the startup script:
- Select the Administration tab then the Commands tab.
- Put this in the Commands text box, then select Save Startup:
1 2 3 4 5 6
#!/bin/sh sed -i -e 's/mppe .*/mppe required,stateless/' /tmp/pptpd/options.pptpd echo "nopcomp" >> /tmp/pptpd/options.pptpd echo "noaccomp" >> /tmp/pptpd/options.pptpd kill `ps | grep pptp | cut -d ' ' -f 1` pptpd -c /tmp/pptpd/pptpd.conf -o /tmp/pptpd/options.pptpd - Go to the Management subtab of Administration and at the bottom select Reboot Router.
This script comes from the PPTP Server Configuration page. The bulk of it is from the iOS 4.3 heading with the addition of the sed line to force encryption.
Configuring the iOS Device
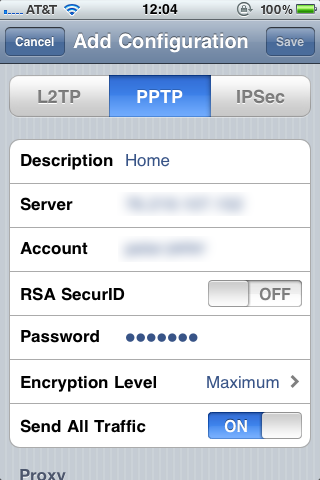
- In the Settings app, choose General then Network then VPN.
- Select Add VPN Configuration...
- At the top choose PPTP and give this configuration a descriptive label.
- For Server put in the IP address of your U-verse residential gateway. (Setting up something like Dynamic DNS with DD-WRT is left as an exercise to the reader.)
- For Account put in the username field from the CHAP-Secrets text box above.
- Leave RSA SecurID off and put in the password field from the CHAP-Secrets text box.
- Under Encryption Level select Maximum.
- Select Save in the upper right hand corner.
Now when you connect to a public network, before starting any applications that will access the internet, go into the Settings app and near the top will be a choice to turn on the VPN. Give it about five or six seconds to make the connection, and you'll then see a blue VPN icon in the status bar at the top next to the WiFi icon.
Acknowledgements
The PPTP Server Configuration was much more helpful than the built in documentation for figuring out what was needed to make this work. A series of posts on the Whirlpool Forums starting with this reply and continuing through a half-dozen more had the final pieces.